Hands-on with Elastic SIEM
I recently found a great tutorial from Gerald Auger on setting up the Elastic SIEM. I have been trying to become more familiar with security solutions that I haven't used before.
The great part about this tutorial is that Gerry provides you with three bullet points that you can add to your resume, once you have completed the setup.
This is what I learned:
Elastic Stack SIEM Configuration and Management: Successfully set up and configured Elastic Stack SIEM in a home lab environment. Demonstrated proficiency in deploying a Kali Linux VM, configuring Elastic Agents for log collection, and forwarding data to the SIEM for effective security event monitoring.
Security Event Simulation and Analysis: Acquired hands-on experience in generating and analyzing security events using Nmap on Kali Linux. Proficient in querying Elastic SIEM to identify and investigate security incidents, enhancing skills in network security monitoring and threat detection.
Visualization and Alerting in SIEM: Developed a custom dashboard in Elastic SIEM to visualize security events, demonstrating skills in data interpretation and pattern recognition. Successfully created and tested alert rules for detecting specific security events, showing competency in proactive incident response and alert management.
The first step is to sign up for the 14-day Free Trial (no credit card required) The setup is much like Wazuh SIEM the way that you add agents using an installation script and setting the daemon as a service.
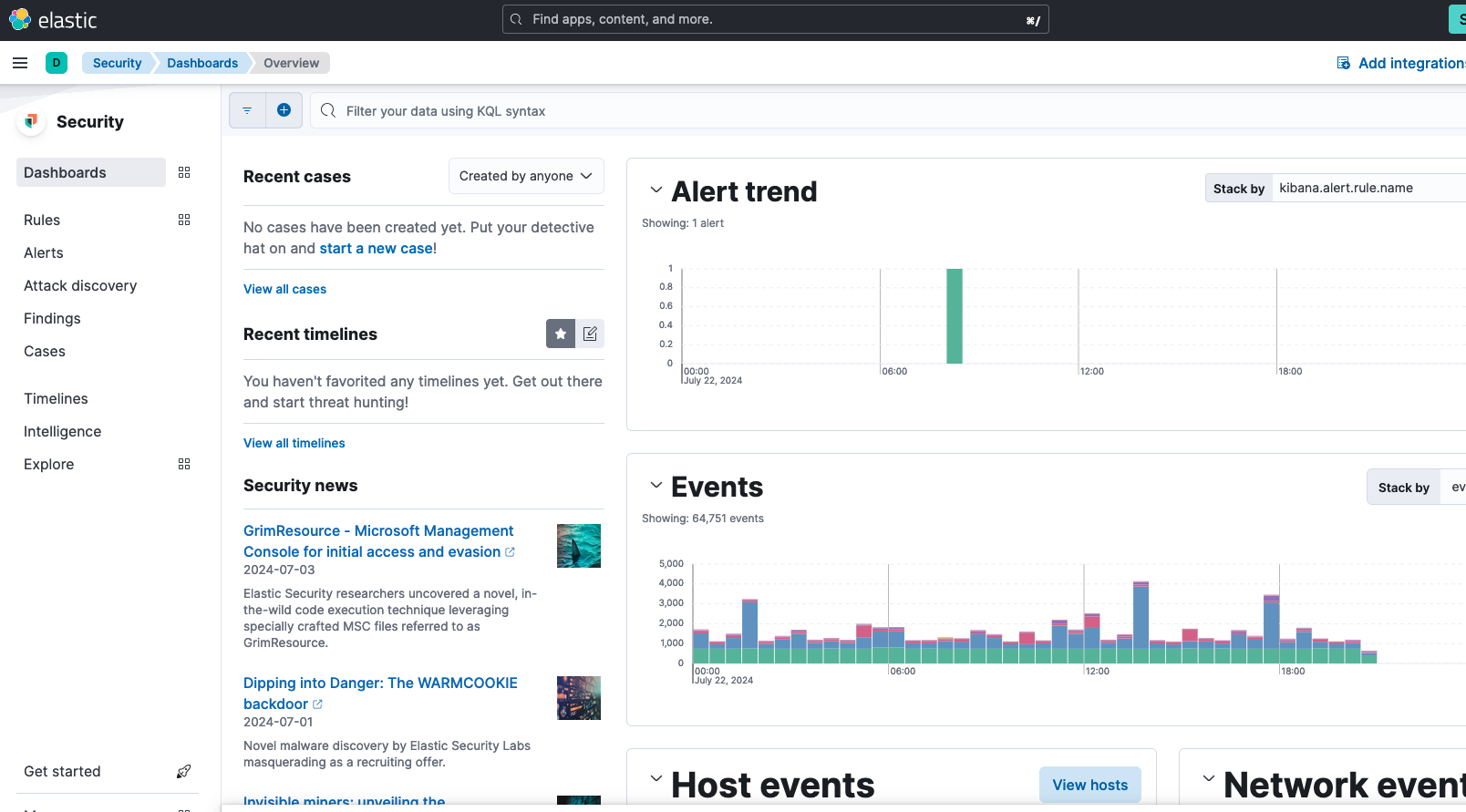
The only thing I did differently was that instead of using VirtualBox, I used an Ubuntu server from Linode that I already had running. I was able to successfully connect the machine and receive data back in the Elastic dashboard.
It would be nice if they had a free Community Edition, instead of just a 14-day trial. I plan to work through setting up some more agents and working through some of the alerts. It is a great tool!
