Hands-on with Wazuh

Wazah is an amazing SIEM (Security Information and Event Management) tool. It is free to use as a self-hosted solution. In this post, I will be explaining some practical ways to use Wazuh to harden the security of an Ubuntu server. If you are unfamiliar with Wazuh, I recommend watching this great video by NetworkChuck to get it up and running.
Once Wazuh is up and running, you will see on the dashboard the section labeled "Latest Scans". At this point, I only have one agent installed, an Ubuntu server running Kali Linux.
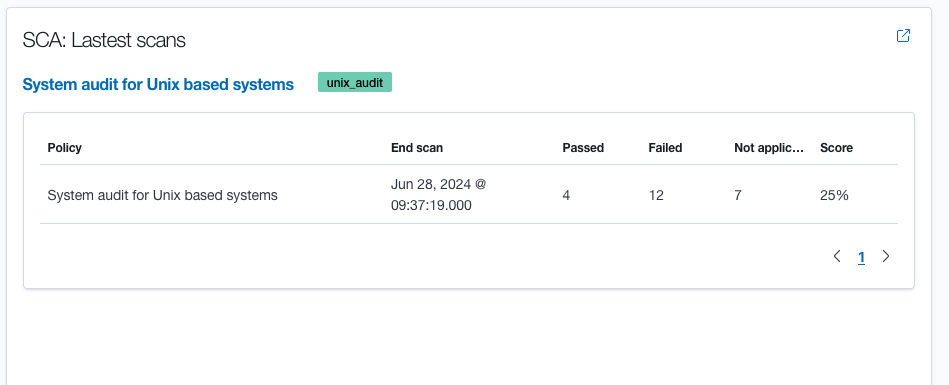
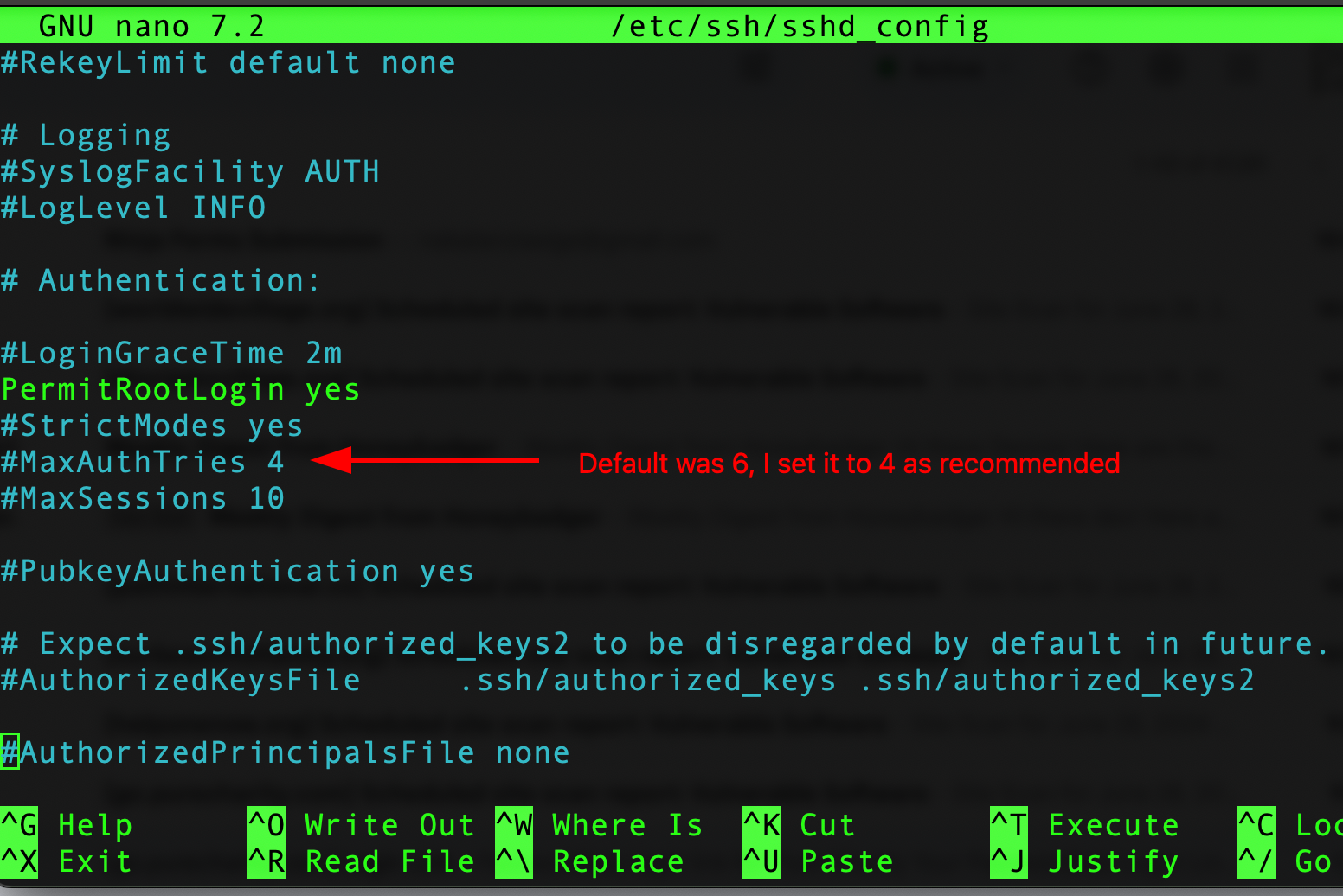
You can see in the image above that I have 12 failed issues on the latest scan. These issues include things such as "SSH Hardening: Wrong Maximum number of authentication attempts". The default MaxAuthTries is set to 6 and the line is commented out, meaning that after you change it to 4, you will need to remove the hashtag for the change to take effect. To do this, you will edit the /etc/ssh/sshd_config file. (Yes, I use Nano, but don't judge me) After making the change and saving it, you will need to run sudo systemctl restart ssh.service for it to take effect. That takes care of one of the 12 issues that Wazuh found, let's move on to the next one.
The next issue we find is Ensure password expiration is 365 days or less this setting can be found in the /etc/login.defs
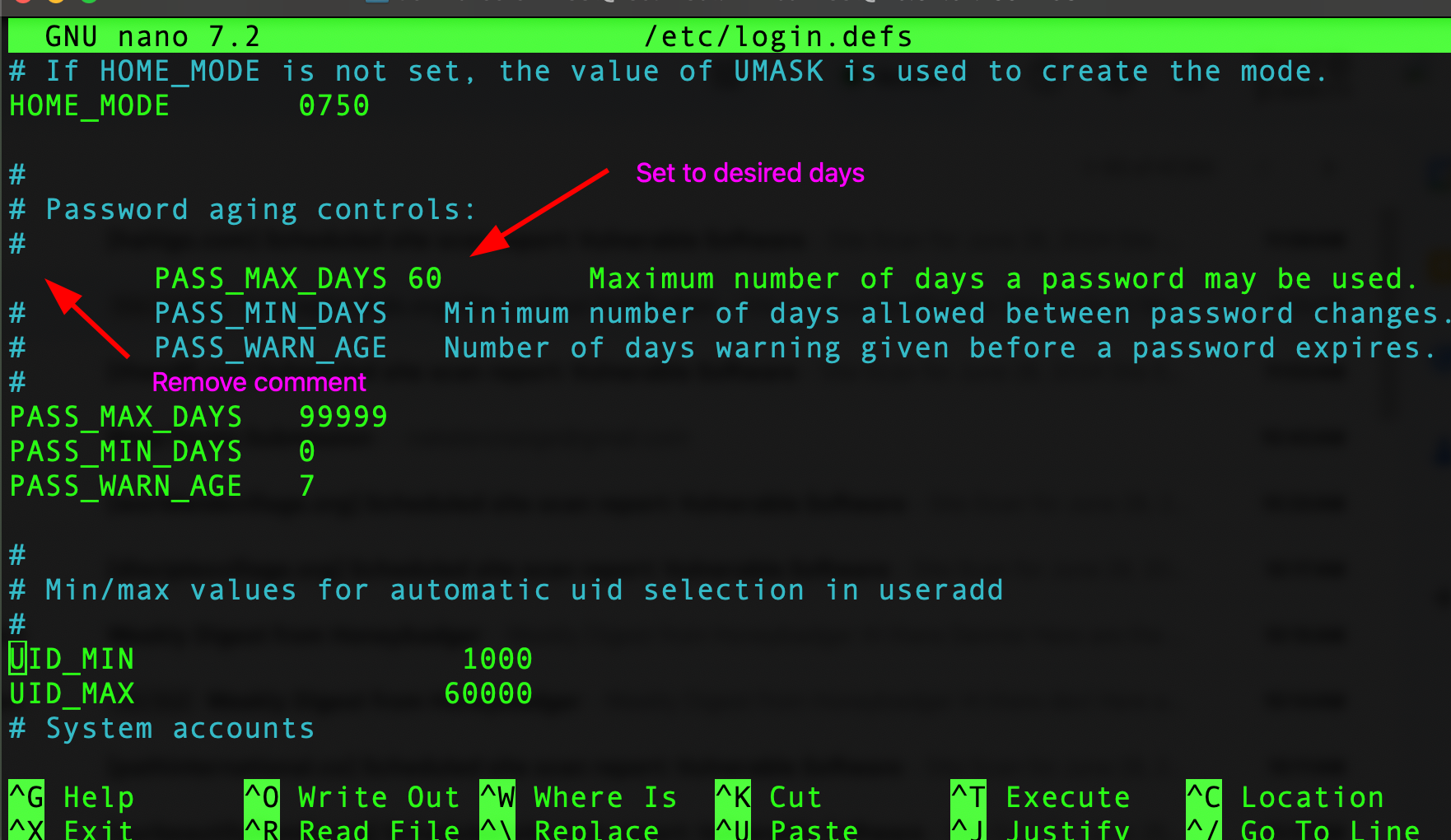
Here you can see that you will need to first remove the hashtag at the beginning of the line, as well as add the number of days 60 after PASS_MAX_DAYS
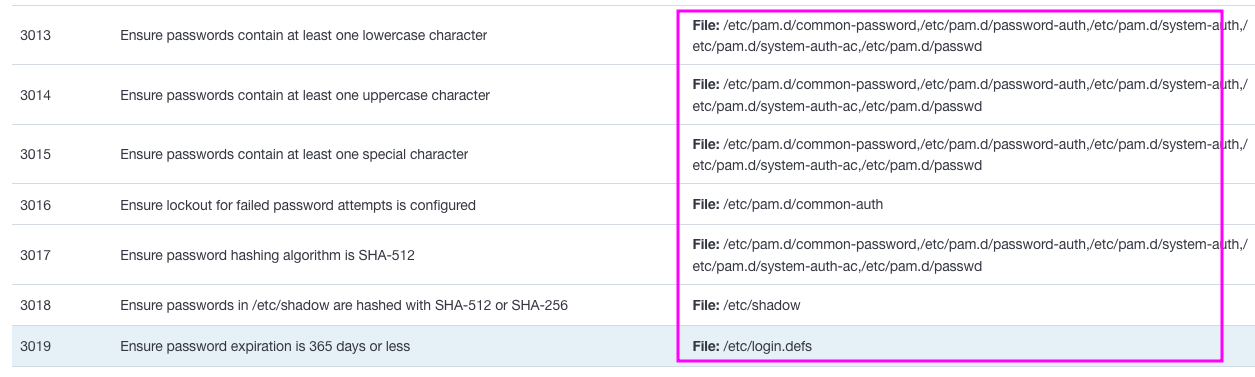
As you work through each issue, you will see that Wazuh tells you which file needs to be edited to resolve the issue.
Wazuh is an amazing tool and it's free. Add all of your machines, both local and cloud-based to check the security and make the necessary improvements. If you have a question of comment, feel free to email me.
