Tailscale for OPSEC

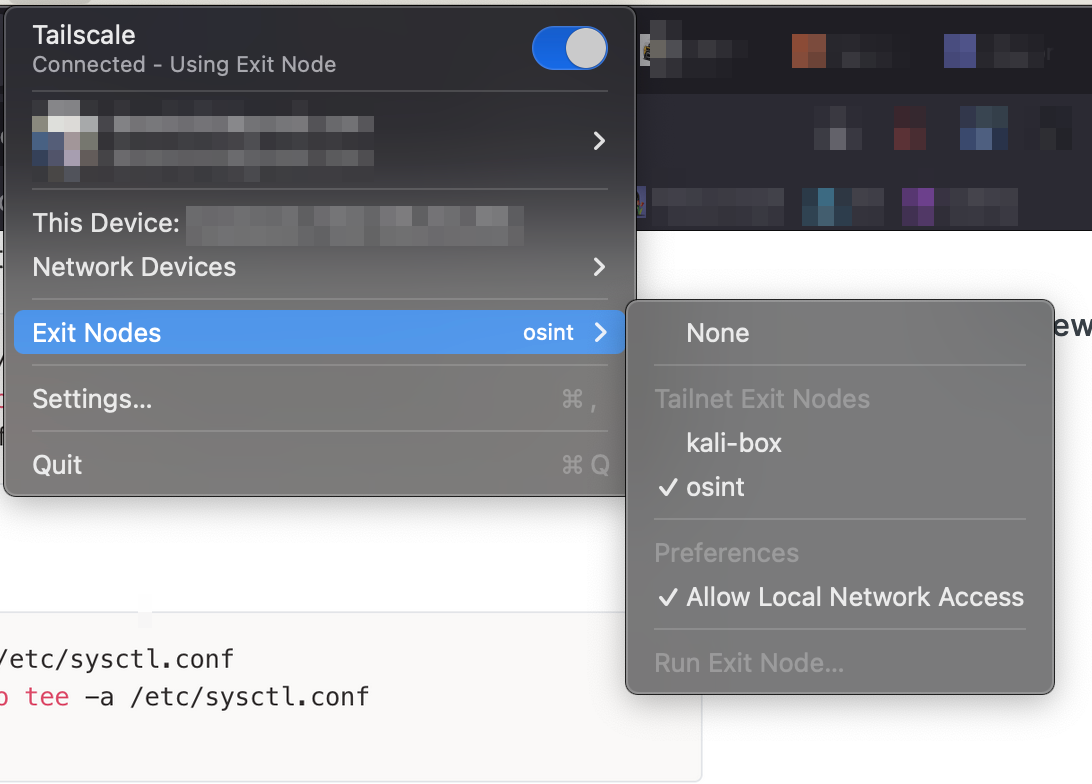
Tailscale is an amazing tool. It allows you to connect all of your machines, without opening ports, etc. One great feature is the ability to use a machine on your tailnet as an "exit node". This means if you have a VPS in Canada, you can enable the exit node feature while working on your laptop and emerge onto the internet in Canada. It's like having a VPN, but on your private network of machines.
One of the difficulties in creating "research accounts" or "sock puppet" accounts is being flagged as suspicious when using a VPN. I'm not 100% sure that using an exit node would help you evade fraud detection, but at minimum, it would provide you with a little more flexibility while researching targets.
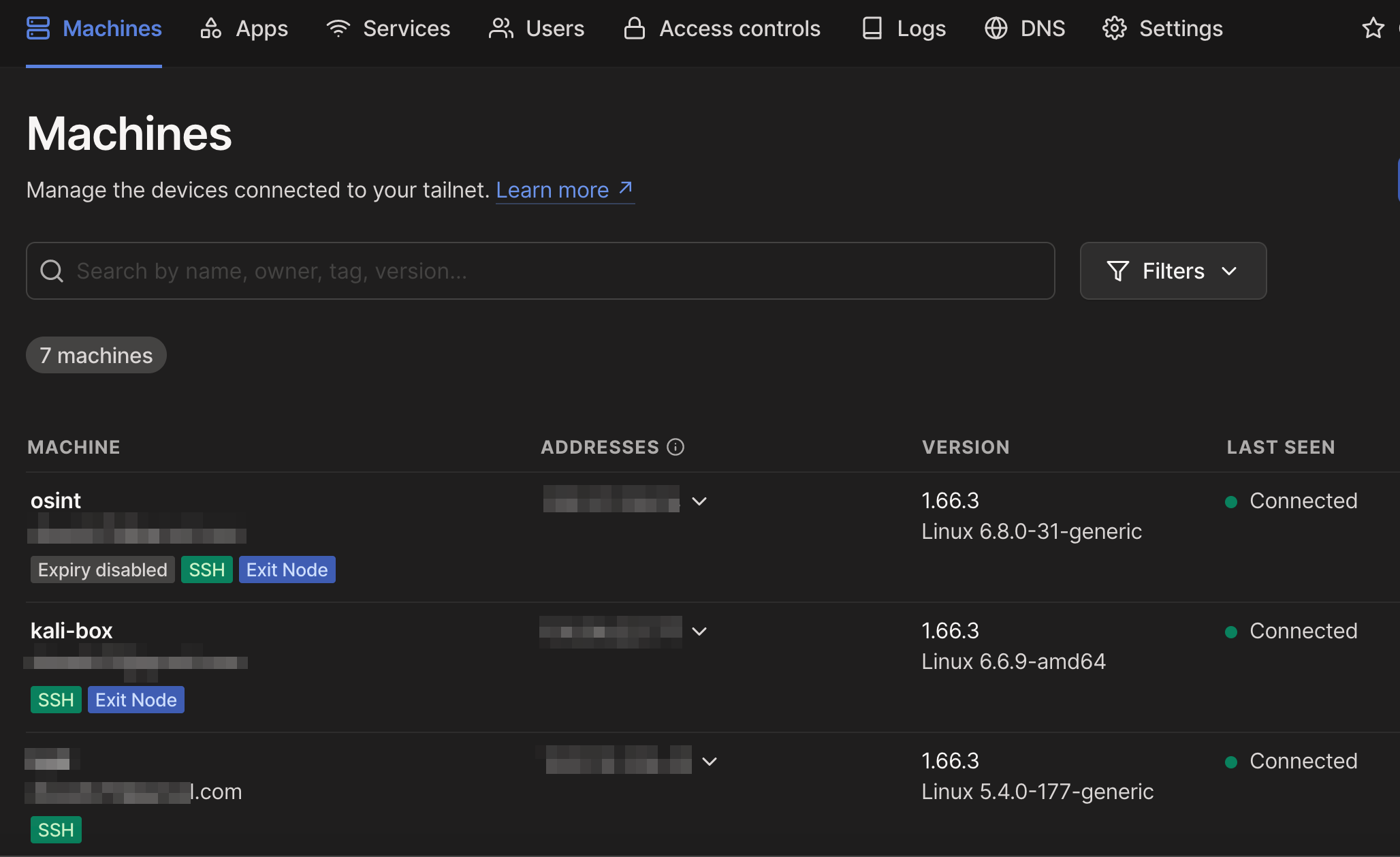
Once you have your machines connected, you can enable SSH and Exit Node by using the following commands.
tailscale set --ssh
tailscale set --advertise-exit-node
When I first attempted to use the exit node feature, I had no internet access. I was a little frustrated and began digging through Google and Reddit trying to find the solution. It seemed that everyone kept mentioning enabling IP forwarding. After digging for a while, I located it here. You just copy the code below.
echo 'net.ipv4.ip_forward = 1' | sudo tee -a /etc/sysctl.d/99-tailscale.conf
echo 'net.ipv6.conf.all.forwarding = 1' | sudo tee -a /etc/sysctl.d/99-tailscale.conf
sudo sysctl -p /etc/sysctl.d/99-tailscale.conf
Once that is done, you can then go to the Tailscale app and choose which exit node to use. You should now emerge onto the internet in the location of your machine or VPS.