The Harvester
I recently discovered a tool called TheHarvester that conducts recon on domain names. The tool gathers names, emails, IPs, subdomains, and URLs by using multiple public resources.
There are several passive modules you can use during your information gathering, however, some require an API key.
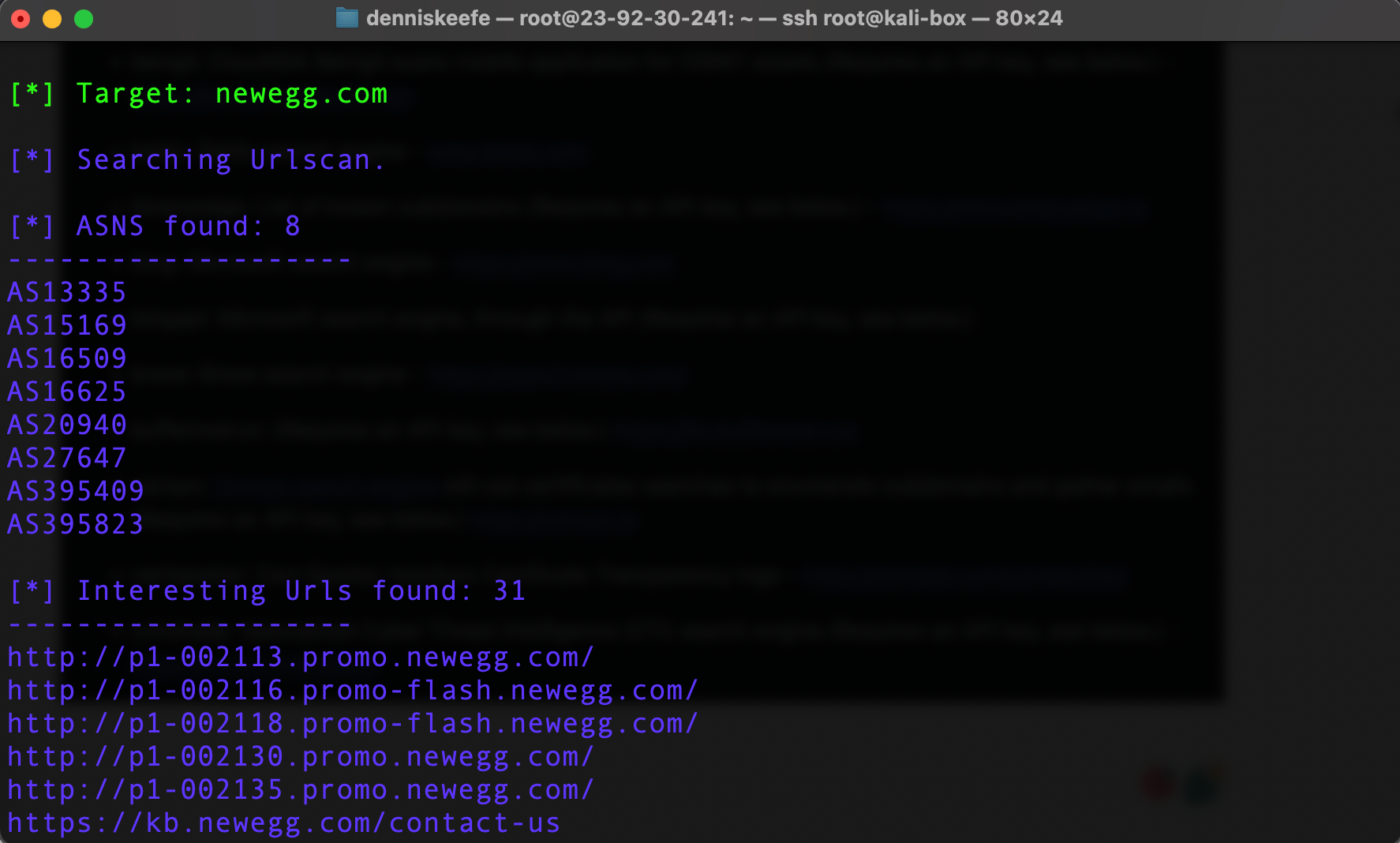
You need to be sure to run theHarvester with a capital H. Here is an usage example:
theHarvester -d newegg.com -b urlscan
The -d identifies the domain and the -b identifies the module you will use to run against the domain. Working through the modules will provide you with different results. You can't add more than one module in the same command, I tried and it won't work.
This tool can provide you with a wide variety of information that you can potentially use for penetration testing and OSINT research. This tool is included in the Kali Linux operating system, but you can also install it in other Linux distros. Give it a try and add it to your toolbox.
